He/Him; Pre-/Post-breach Cyber Responder
Joined June 2011
- Tweets 74,237
- Following 7,500
- Followers 3,295
- Likes 19,311
virustotal.com/gui/file/ab62…
Too busy with IR's this week for RE :)
Andre Gironda retweeted
View the long form here:
malasada.tech/pdfchampions-y…
Andre Gironda retweeted
YAPA is Yet Another PDF App that Luke Acha (@luke92881) mentions here: blog.lukeacha.com/2025/11/fa…
Andre Gironda retweeted
View the Any Run session here:
app.any.run/tasks/07e8ff42-e…
Andre Gironda retweeted
The interesting part about this one is that it has a loader capability. That is - it takes the code that was passed as an argument. It will check its cache to see if it was already compiled. If it wasn't already compiled, it'll compile it into an assembly object on line 56 and add it to the cache on line 57. Note, this remains in memory, and it does not get saved to disk. It executes the code on line 81.
Andre Gironda retweeted
It downloads this mozlz4 file to change the default search engine. The browser hijacker redirects to Google search.
Andre Gironda retweeted
PDFChampions is a YAPA Browser Hijacker with Loader capabilities.
7c5004c9d3ed4325c547ec0127d59205529f4574444a9e74dc108b0783d6e392
pdfchampions[.]com
downloadive[.]com
champion.pdfchampions[.]com
api.mekanfig[.]com
more.mariosearch[.]com
hxxps[:]//pdfchampions[.]com/pdfchampions
hxxps[:]//pdfchampions[.]com/thanks?book=1
hxxps[:]//downloadive[.]com/puoyder/o/PDFChampions.exe
hxxps[:]//champion.pdfchampions[.]com
hxxps[:]//api.mekanfig[.]com/api/v1/
Andre Gironda retweeted
Fantastic research by @MalasadaTech808 on PDFChampions. Code-signed "Flooencia Media LLC"
I don't think code-signing handles Registered Agents well. I keep reporting code-signing certificates for businesses at this address.
PDFChampions is a YAPA Browser Hijacker with Loader capabilities.
7c5004c9d3ed4325c547ec0127d59205529f4574444a9e74dc108b0783d6e392
pdfchampions[.]com
downloadive[.]com
champion.pdfchampions[.]com
api.mekanfig[.]com
more.mariosearch[.]com
hxxps[:]//pdfchampions[.]com/pdfchampions
hxxps[:]//pdfchampions[.]com/thanks?book=1
hxxps[:]//downloadive[.]com/puoyder/o/PDFChampions.exe
hxxps[:]//champion.pdfchampions[.]com
hxxps[:]//api.mekanfig[.]com/api/v1/
Andre Gironda retweeted
#NOVA #Ransomware launched Affiliate Panel for the 2nd time!
cceoxb5youzqo2uk7t7274ittlph…
Git: github.com/TheRavenFile/Dail…
#Malware #Infosec #Security #OSINT #DarkWeb #DeepWeb #ThreatIntel #Hack
Andre Gironda retweeted
3/
However, the #sidewinder still using the same domain and C2 server to continue phishing.
ref: hunt.io/blog/operation-south…
Andre Gironda retweeted
2/
Research on #Operation #SouthNet by @Huntio also revealed that same pages was observed at https://mailcbmgovmm[.]pages[.]dev which is now reported as phishing.
Andre Gironda retweeted
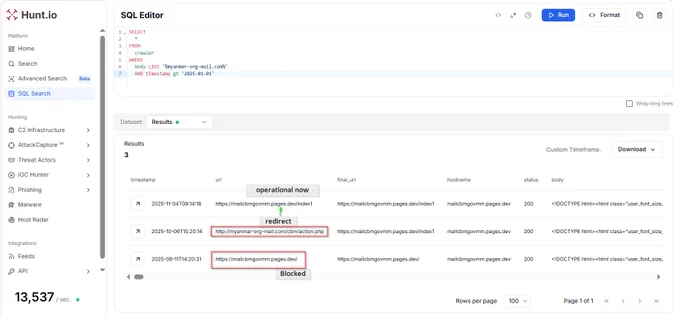
#APT #Sidewinder targets #Myanmar Central Bank
1/
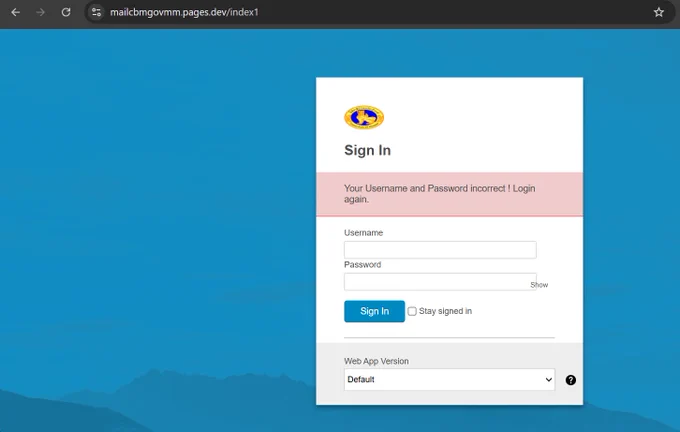
Using @Huntio, I have tracked a new operational Fake Zimbra page "https://mailcbmgovmm[.]pages[.]dev/index1" which exfiltrate info to "myanmar-org-mail[.]com/cbm/action1[.]php/".
@500mk500 @MichalKoczwara @malwrhunterteam
Andre Gironda retweeted
Tracking a large-scale Booking-themed phishing campaign targeting hotel partners, hundreds of fake domains impersonating Booking.com used to steal credentials and deliver malware.
query:
urlscan.io/search/#hash%3A78…
report: blog.sekoia.io/phishing-camp…
Andre Gironda retweeted
Malicious NuGet packages drop disruptive 'time bombs' - @billtoulas
bleepingcomputer.com/news/se…
bleepingcomputer.com/news/se…
Andre Gironda retweeted
CVE-2025-64459 - PoC for Django QuerySet _connector SQL Injection
#Pruva repro and report: gist.github.com/N3mes1s/2dbc…
Advs: djangoproject.com/weblog/202…
🚨🚨Django Patches Two High-Severity Vulnerabilities
CVE-2025-64459(CVSS 9.1): High-Severity SQL Injection via _connector Keyword
CVE-2025-64458(CVSS 7.5): Moderate Denial-of-Service (DoS) on Windows via Unicode Redirects
ZoomEye Dork👉app="Django"
189.7k+ exposed instances discovered.
ZoomEye Link: zoomeye.ai/searchResult?q=YX…
Refer:
1. djangoproject.com/weblog/202…
2. hub.zoomeye.ai/
#ZoomEye #cybersecurity #infosec #OSINT
Andre Gironda retweeted
Microsoft has discovered a new type of side-channel attack against streaming-mode language models using network packet sizes and timings. msft.it/6018tJAkA
An attacker in a position to observe the encrypted traffic could use this type of side-channel attack to conclude language model conversation topics. This could put the privacy of user and enterprise communications with chatbots at risk despite end-to-end encryption via TLS.
We worked with multiple cloud providers of language models to mitigate the risk, and ensured that Microsoft-owned language model frameworks are protected. Learn more: