Senior Threat Intel Advisor @TeamCymru | Co-founder @CuratedIntel | Co-author @SANSForensics FOR589 | Co-founder @BSidesBournemth | @darknetdiaries #126: REvil
🇬🇧
Joined March 2013
- Tweets 12,637
- Following 3,334
- Followers 36,659
- Likes 36,676
Pinned Tweet
New Blog 👀
This blog discusses the topic of cybercrime counterintelligence to highlight the growing threat toward the cyber threat intelligence (CTI) and law enforcement (LE) communities ⚠️
🔗 sans.org/blog/for589-cybercr…
Will retweeted
New Blog from the B2600 crew!
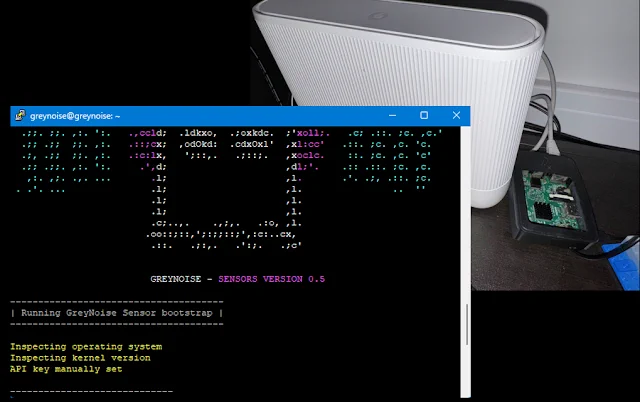
We recently embarked on a research project involving honeypots posing as legitimate corporate gateways to attract threats towards them.
Thanks to @GreyNoiseIO for their community services!
blog.bournemouth2600.org/202…
Latest RedTail IOCs via @bournemouth2600: github.com/Bournemouth2600/B…
Another JA4+ Win 🏆
Been tracking the #RedTail Bot campaign (akamai.com/blog/security-res…) this week & using the Wireshark JA4 plugin.
The RedTail exploit source IPs all use the same JA4 fingerprint, which defenders could use for detection: "t13i170900_5b57614c22b0_78e6aca7449b"
IOCs collected at the time of publication are available to the wider community via NVISO on ThreatFox here:
threatfox.abuse.ch/browse/ma…
🆕 Checkout the blog between @NVISOsecurity & @TeamCymru all about #VShell, which has been used a lot over the last year (over 1,500 servers!), primarily used for long-term espionage activities 🌍🇨🇳
Including NetFlow Analysis 👀
🔗 nviso.eu/blog/nviso-analyzes…
Will retweeted
We are thrilled to have collaborated with @NVISOsecurity on their latest #VShell research! Our insights helped shape the findings on this evolving threat. Check out their blog for the full details. 🐉🐦⬛
Our NVISO #IncidentResponse Team has been tracking #VShell campaigns worldwide! More than 1,500 active VShell servers were uncovered, each capable of giving attackers remote control over compromised networks. Read the report here 👇
nviso.eu/blog/nviso-analyzes…
Two bombshell stories all cybersecurity professionals must read:
1. Ex-ASD boss of US Exploiter Developer sold exploits to the Russians
techcrunch.com/2025/11/03/ho…
2. Employees of a US ransomware negotiation firm ran attacks with BlackCat ransomware
chicago.suntimes.com/the-wat…
Not to mention, lots of tool reuse: CyberDuck, Mimikatz, CobaltStrike, SystemBC, HRSword, RSAT. And tons of RMMs; AnyDesk, Chrome Remote Desktop, Distant Desktop, GoToDesk, QuickAssist, and ScreenConnect
New blog by @TalosSecurity on Qilin!
TL;DR
- In H1 2025, Qilin published victim info on its leak site at a pace of more than 40 per month
- Manufacturing sector is most affected, making up 23% of victims
blog.talosintelligence.com/u…
After filtering for the largest outflow, the AI analyze feature of @arkham also picked up a Wallet Consolidation. Cool feature 👍
I’ve clustered these CharmingKitten BTC addresses into @arkham and identified some TXs with KYC exchanges like Binance, Coinbase, and Kraken. Some good leads for investigators here: intel.arkm.com/explorer/enti…
Spotted a rather @TeamCymru looking fountain here in the Netherlands 🇳🇱 this week! 📸
This further shows all of the tools mentioned in the Capita breach were already well-known BlackBasta tradecraft: Cobalt Strike, Bloodhound, Rclone
Additional Resources for Threat Hunters:
a) BlackBasta Group Profile in the Ransomware Tool Matrix github.com/BushidoUK/Ransomw…
b) BlackBasta Group Profile in the Ransomware Vulnerability Matrix
github.com/BushidoUK/Ransomw…
Despite Capita having an EDR, a SIEM, and a SOC, the P2 alerts were missed and containment delayed. ⏰