Electrical engineer Hacking the planet, full time, in pink. Always curious, constantly learning. Bug bounty Hunter on @bugcrowd and @hacker0x01
127.0.0.1
Joined January 2023
- Tweets 82
- Following 201
- Followers 298
- Likes 415
SheilaC retweeted
I’ve noticed that most new folks who reach out for guidance in bug bounty feel overwhelmed early on trying to learn everything at once. That often leads to half-baked knowledge across multiple areas and slower overall progress.
Here's what I recommend instead 👇
1/
Pick one vulnerability type and go all in.
Master the ins and outs of that category - how it works, how it breaks, real-world examples, and ways to find it.
Once you’ve got depth in one area, the rest will follow naturally.
2/
To put this into perspective, here’s a snapshot of the types of issues I’ve reported over the last 5 years - gradually expanding focus as I grew more confident:
2020:
• Local cache issues
• Rate limit issues on Login
• Session invalidation
• MFA bypass
2021:
• Rate limit
• MFA bypass
• CSRF
• IDOR
• RBAC
2022:
• CSRF
• IDOR
• RBAC
• XSS
• Business logic
• Info disclosure
2023:
• Everything from 2022 +
• BBP automation
• Cache deception
• DoS Issues
• Subdomain takeover
• Auth bypass / misconfig
• SQLi
• SSRF
• RCE
2024:
• Everything from 2023 +
• AI-related issues
• Vhost misconfigurations
2025:
• Everything from 2024 +
• Many more new things that I will talk about soon :)
3/
There are more, of course, but this covers most of what’s worked well for me.
The key takeaway: you don’t need to know everything.
Play to your strengths. Stay consistent. And let your scope expand naturally.
Hope this helps someone starting out 💪
SheilaC retweeted
I'm a hacker and AI researcher who has reported vulnerabilities to OpenAI, Google, and others. I wrote this guide as a reference of all of the ways that you can hack AI.
It has saved me hours. Bookmark this if you need a reference for what all to try (AND includes mitigations).
Perks of being a Bug Bounty Hunter: Found a bug in GitHub, got it accepted, and now I have GitHub Pro for FREE… FOREVER.
SheilaC retweeted
One day, the technique for exploiting this vulnerability will be available. Not today, but one day.
Working with other bug hunters makes a huge difference. Two minds bouncing ideas off each other leads to peak efficiency.
SheilaC retweeted
You should read the new article.
bytebloggerbase.com/main/667…
bytebloggerbase.com/main/667…
bytebloggerbase.com/main/667…
Show your support and start publishing your articles with bytebloggerbase.com.
#bytebloggerbase #articles #infosec #cybersecurity
SheilaC retweeted
Google Dorks for Bug Bounty
Input your target to generate Google Dork links for easy OSINT recon #bugbountytips
taksec.github.io/google-dork…
SheilaC retweeted
My favorite Google dork flow:
1. Start w/ "site:<domain>"
2. Remove stuff "-www"
3. Keep reading and removing until you get to the fun stuff
Example:
site:tesla .com -www -shop -share -ir -mfa
#bugbountytips #bugbounty #hacking #infosec #cybersecuritytips #recon #bugbountytip
Authentication Bypass via forgot password
18 days in triage is never a good sign though. #bugbounty
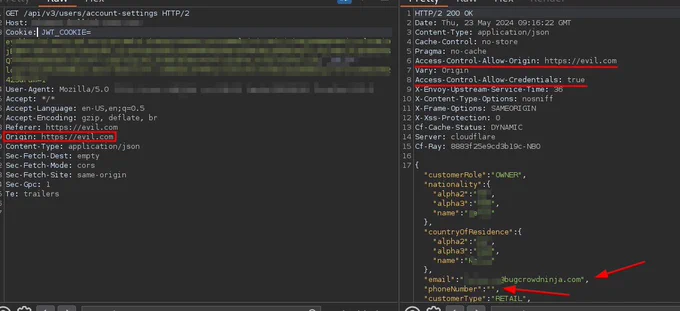
Today I found a promising CORS misconfiguration that should have leaked PII!
Here’s a critical detail that’s often missed. For successful exploitation, the ‘SameSite’ attribute on the cookie must be set to ‘Lax’ or ‘None’. In this case it was set to ‘Strict’🛡️ #BugBounty #CORS
SheilaC retweeted
Authentication Bypass Via Response Manipulation
After Registration, it said waiting for admin approval
tried to sign in and capture the request I found in the response {"role": "blocked"}
#bugbountytip #bugbounty #bugbountytips
My first paid bug on Bugcrowd was an Authentication Bypass. I will definitely push a write up after I’m done with my research! :)