C•S INSTRUCTOR//Purple Teamer // ISC² certified //InfoSec //Documenting My Journey into Cybersecurity & I Post Educative Content// Turn on Post Notis 🔔
my links 🔗 👇
Joined October 2024
- Tweets 18,427
- Following 266
- Followers 21,982
- Likes 5,855
Pinned Tweet
Cybersecurity Roadmap: Step-by-Step Guide for Aspiring Professionals
Embarking on a cybersecurity journey can be challenging, but with the right plan, you can progress steadily and achieve your goals. Based on my personal journey as a penetration tester in training, here’s a roadmap tailored to aspiring cybersecurity professionals, infused with my insights and practical experiences.
[A thread 📷]
Abdulkadir | Cybersecurity retweeted
I am using these guidelines to start my journey as a cybersecurity Expert.
You can wish me well if you want to.
Cybersecurity Roadmap: Step-by-Step Guide for Aspiring Professionals
Embarking on a cybersecurity journey can be challenging, but with the right plan, you can progress steadily and achieve your goals. Based on my personal journey as a penetration tester in training, here’s a roadmap tailored to aspiring cybersecurity professionals, infused with my insights and practical experiences.
[A thread 📷]
SECURITY+ KNOWLEDGE CHECKPOINT
A security analyst notices numerous failed login attempts from multiple IP addresses across different geographic regions, all targeting different user accounts within the same organization. Which type of attack is MOST likely occurring?
A. Credential Stuffing
B. Password Spraying
C. Brute Force Attack
D. Reconnaissance Scanning
Abdulkadir | Cybersecurity retweeted
Being a Nigerian twitter
Is like a daily cycle of ragebait
Are we all mad in this country 😭😭😭
Abdulkadir | Cybersecurity retweeted
I remember when i used to install kali regularly cause of one issue or the other, now I try to fix these issues without reinstallation, kinda miss the installation stage.
Abdulkadir | Cybersecurity retweeted
There’s no talent shortage in cybersecurity. It’s just cert companies selling dreams as "career paths." Every few months they shout about "millions of open jobs" right before dropping a $1,200 course and certifications.
Abdulkadir | Cybersecurity retweeted
A lot of nigerians both old and young
Are seriously regretting not starting fraud earlier or at all sef
But are too scared to admit it
Abdulkadir | Cybersecurity retweeted
Sponsor: ME
I gave him discount on a laptop
@cyber_razz we have a student
@Val_Gadget
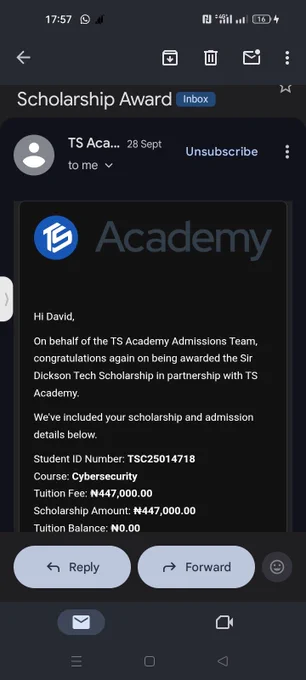
I've got a budget of 200k and I can't even access the money until 7th of November, which is why I put my start-up date in November. I was hoping I would get the scholarship and by the time training starts I would have gotten a laptop. I chose Cybersecurity by the way
Abdulkadir | Cybersecurity retweeted
Let’s break down CIDR notation like you’re hearing it for the first time:
CIDR = Classless Inter-Domain Routing
It defines how many bits are used for the network part of an IP address.
Example:
192.168.1.0/24
That /24 means the first 24 bits are for the network, and the rest are for hosts.
Each IP address has 4 octets (sections).
Each octet = 8 bits.
So:
11111111 in binary = 255 in decimal.
This is key to understanding subnet masks!
Let’s see how it works:
/8 = 11111111.00000000.00000000.00000000 → 255.0.0.0 → 16,777,214 hosts
/16 = 11111111.11111111.00000000.00000000 → 255.255.0.0 → 65,534 hosts
/24 = 11111111.11111111.11111111.00000000 → 255.255.255.0 → 254 hosts
/30 = 11111111.11111111.11111111.11111100 → 255.255.255.252 → 2 hosts
/32 = 11111111.11111111.11111111.11111111 → 255.255.255.255 → 1 host
What this means in real life:
•/8 = Over 16 million IPs (used by huge networks)
•/16 = 65k+ IPs (used by ISPs or large companies)
•/24 = 254 usable IPs (used in homes or small offices)
•/30 = 2 IPs (used in point-to-point links between routers)
•/32 = A single device (often used in firewall rules or identifying one server)
Easy trick:
Each 255 = 8 bits set to 1 in binary = /8
So:
•255.255.255.0 = /24
•255.255.255.192 = /26 (because 192 in binary is 11000000 → 2 more bits)
CIDR gives us more flexibility than the old Class A/B/C system.
We can break networks into just the sizes we need — no waste.
If you’re in networking or cybersecurity, CIDR is a concept you’ll use all the time.