dragon21 retweeted
As far as I'm concerned, these seems to come in ZIP archives with the LNK calling the BAT and at the very least, get distributed through #WhatsApp.
And potentially through cliente[.]rte[.]com[.]br a few days ago.
Don't have access to the WhatsApp Web on the compromised systems.
'HealthApp-a00697.bat' is a FUD from Brazil @abuse_ch
bazaar.abuse.ch/sample/cfe65…
expansiveuser(.)com
Same domain as below 👇
dragon21 retweeted
#YoroTrooper Operation Update
FoalShell reverse shells and StallionRAT (remote access trojans) controlled via Telegram.
P2 PDB looks like last report.
bi-zone.medium.com/cavalry-w…
dragon21 retweeted
Golang reverse engineering walkthrough! A challenge we solve with three different approaches: (1) static analysis with IDA, (2) dynamic analysis in a debugger and (3) patching the binary and switching to a desired code path 😎 piped.video/4-7zcq5-cNA
dragon21 retweeted
I probably should have known this, but apparently Copilot outputs everything in Markdown
Nice to see even AI struggles with properly escaping multi-line KQL queries in markdown, lol
dragon21 retweeted
Found Related #spyware #campaign Sample / Domain using @Huntio
9d3ac92937c8986ce55b308c60ae8f9a
https://signal-encryption-service[.]ct[.]ws/signsdhfg6aug/signsdhfg6aug/Signal_Encryption_Plugin_V4.7.3.apk
@500mk500 @LukasStefanko
Ref:
We identified two campaigns targeting #Android users with previously undocumented spyware impersonating #Signal and #ToTok via deceptive websites
welivesecurity.com/en/eset-r… #ESET #ESETresearch
dragon21 retweeted
🚨 Malicious PyPI package spotted: “soopsocks” hit 2,653 downloads before takedown.
Advertised as a SOCKS5 proxy, it secretly:
– Dropped a Go-based backdoor (_AUTORUN.EXE)
– Ran PowerShell + VBScript
– Changed firewall rules
– Exfiltrated system data
Full report ↓ thehackernews.com/2025/10/al…
dragon21 retweeted
So that's what it was .... Cc @smica83
trendmicro.com/en_gb/researc…
As far as I'm concerned, these seems to come in ZIP archives with the LNK calling the BAT and at the very least, get distributed through #WhatsApp.
And potentially through cliente[.]rte[.]com[.]br a few days ago.
Don't have access to the WhatsApp Web on the compromised systems.
dragon21 retweeted
The Clop ransomware gang confirmed to BleepingComputer they are behind the emails, claiming they exploited an Oracle bug to steal the data.
“We not prepared to discuss details at this time. Soon all will become
obvious that Oracle bugged up their core product and once again, the task is on clop to save the day. We do not damage to systems and only expect payment for services we provide to protect hundreds of biggest companies in world.”
Emails claim Oracle data theft in new Clop-linked extortion campaign - @LawrenceAbrams
bleepingcomputer.com/news/se…
bleepingcomputer.com/news/se…
dragon21 retweeted
Learn how malware is linked to its operators and what that tells us about tradecraft. This case study examines the Bookworm RAT and its use by Chinese APT Stately Taurus. The analysis demonstrates the evidence-based approach of our Attribution Framework. bit.ly/3Kl2b0X
dragon21 retweeted
Proactive detection for UNC6040 (aka ShinyHunters)
cloud.google.com/blog/topics…
Google's Threat Intelligence Group outlines security strategies to defend against UNC6040, a financially motivated threat actor using voice phishing (vishing) to compromise Salesforce environments. The attackers trick users into approving malicious connected apps, enabling data theft. The blog provides proactive hardening measures, logging protocols, and detection techniques to protect SaaS platforms, especially Salesforce. Below is a Seninel KQL detection for UNC6040 built based on GTIG report.
detections.ai/share/rule/5LA…
#Cybersecurity #UNC6040 #ShinyHunters
dragon21 retweeted
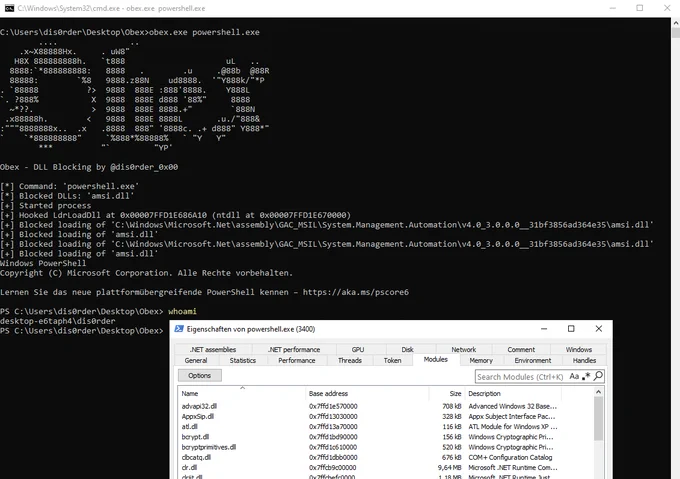
Block EDR dynamic libraries from loading.
By using debugging API, exception handling and simple hooks, one can spawn a clean process (PoC blocks amsi.dll).
A nice post by @dis0rder_0x00
Source: github.com/dis0rder0x00/obex
#redteam #maldev #malwaredevelopment
dragon21 retweeted
🚨 A single click on a shortcut file was enough.
Confucius hackers just stole passwords, screenshots & files across Pakistan’s government and defense networks.
They hid the breach behind routine Windows .LNK files — a trick most security tools missed.
Read ↓ thehackernews.com/2025/10/co…
🆕Recent additions to LOLBAS-Project.github.io:
• iscsicpl.exe for DLL exec+UAC bypass
• eudcedit.exe for UAC bypass
• reset.exe/change.exe/query.exe for proxy exec
• pixtool.exe/applauncher.exe/mpiexec.exe for dev tool proxy exec
⭐Nearly 8,000 GitHub stars - thank you all!
dragon21 retweeted
🛡️ 𝐀 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐧𝐠𝐢𝐧𝐞𝐞𝐫'𝐬 𝐆𝐮𝐢𝐝𝐞 𝐭𝐨 𝐌𝐂𝐏
If you need to learn how to test & secure MCPs in your org in a hurry...
Get up to speed in 10min + a free MCP security cheatsheet of exactly what to look for.
dragon21 retweeted
🚨 Upcoming Secure by Default Settings Changes for Exchange and Teams APIs
Starting late October to November 2025, Microsoft will require admin consent for third-party apps accessing Exchange and Teams content via Microsoft-managed default consent policy. Finally!👏
admin.microsoft.com/?ref=Mes…
#Cybersecurity #SFI #SecurebyDefault
dragon21 retweeted
⚡️NEW Module: Analyzing Obfuscated Shellcode
- Hands-on
- Live analysis in your browser - zero setup
Beginner-friendly introduction to obfuscated shellcode extraction and analysis 👇
#ReverseEngineering #Malware
aceresponder.com/learn/obfus…
dragon21 retweeted
Ongoing activity uses #blobURLs to deliver #phishing pages. These pages dynamically construct malicious content in the browser's memory at runtime to bypass network analyzers. Details and recent examples at bit.ly/3VIYCnQ
dragon21 retweeted
What separates Managed EDR from just “having EDR”?
Alerts are easy. Context isn’t. 🔎
Where machines catch the noise, humans connect the dots, and hackers get wrecked.
Check out real examples showing why the “managed” part makes all the difference: okt.to/VdJOjZ
dragon21 retweeted
🔸 "lmg_Lena_Paul_OnlFans_1781.zip": e7a71c464583de2c94f1414d741a1ababaffebc426c1ca65819681bff9764b18.
Fully undetectable by 65 AV engines, but flagged by IDS and Sigma rules ✔️
⛓️ DownloadString (remote content in valid image) → Regex extract (BaseStart/BaseEnd) → Base64 decode → Reflective .NET Assembly.Load → Resolve type (ClassLibrary1.Home) → GetMethod(VAI) → Malicious execution and persistence (scheduled task).
Infection flow widely seen lately 📈
Next stages:
- https://cardvaultcc[.]com/txt/aaa.png
- https://pastee[.]dev/r/cZkG3nzD/0
- ohmy0hs.dynuddns[.]net
H/T @malwrhunterteam @cyb3rops
dragon21 retweeted
Thread: 1/4
Bug Bounty Tip 🧵: Your next critical finding might be hiding in a publicly exposed .git directory.
It's a common misconfiguration that leaks the entire code history, including secrets, old endpoints, and unpatched vulns.
#bugbountytips #infosec