I'm also @taviso@social.sdf.org
California
Joined April 2008
- Tweets 9,209
- Following 633
- Followers 130,455
- Likes 8,811
Pinned Tweet
You can now jailbreak your AMD CPU! 🔥We've just released a full microcode toolchain, with source code and tutorials. bughunters.google.com/blog/5…
Tavis Ormandy retweeted
We’re excited to see the security and OSS communities engage on vulnerability disclosure in light of new AI technologies that we believe will enable both defenders and attackers alike. Existing and emerging norms around disclosure are important debates, and we’ve noted the feedback. Thanks! Also want to share some additional thoughts. 1/10
Tavis Ormandy retweeted
On the pod this week, I saved a closing shoutout for @taviso and his work at P0
piped.video/qPj9_8azAvk?t=8398
I have many good stories from my time here, maybe I'll share some later! And yes, the leaving tradition is real, and yes they got me 😆
A personal update... after nearly 20 years at Google, today is my last day! I'm going to be working on independent research for the foreseeable future, then who knows! I've worked with so many talented people, made so many friends and seen incredible research over the years 🫡
I have a (dumb) theory about Intel. They used to ship beautiful printed manuals anywhere in the world for free if you called them. That program made a lot of engineering students customers for life. Then some middle manager killed it, and probably got a promotion.
Hey... quick question, why are anime catgirls blocking my access to the Linux kernel? 😸
lock.cmpxchg8b.com/anubis.ht…
Tavis Ormandy retweeted
EntrySign was nominated for two Pwnies (best crypto bug and best desktop bug)! 🥳
piped.video/live/TuKPA-CeDFA…
@__spq__ @sirdarckcat @taviso
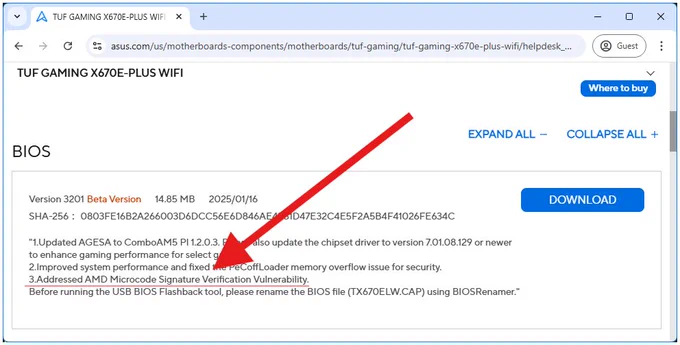
This is neat, using EntrySign to backport microcode patches to EOL systems without BIOS updates. github.com/divestedcg/real-u…
Tavis Ormandy retweeted
Back in 2023, the assessment of the pre-authentication vulnerability in SSH was that it wasn't exploitable on Linux.
For my OffensiveCon 2025 keynote, I wrote enough of an exploit to show, with the right heap groom and stabilization, it's likely exploitable. Then I tried to have AI do it.
Up to @taviso whether that merits switching to Windows 98 :)
piped.video/watch?v=Y1naY3gu…
Tavis Ormandy retweeted
The recording of our OffensiveCon presentation about EntrySign is live! piped.video/sUFDKTaCQEk
Slides at entrysign.top
@sirdarckcat @__spq__
Tavis Ormandy retweeted
Fuzzing Windows Defender in the Honggfuzz+IntelPT (hardware) mode
scrapco.de/blog/fuzzing-wind…
by @buherator
The code and tutorials are here if the link doesn't work! 😒 github.com/google/security-r…