Software, performance, optimization, programming languages, security, open source, #CarbonLang lead, #LLVM, #Clang, C++. 🏳️🌈 he / they
San Jose, CA
Joined November 2011
- Tweets 5,080
- Following 232
- Followers 14,411
- Likes 4,763
Pinned Tweet
FYI:
I'm not engaging on Twitter. It's leadership is undermining saftey and enabling hateful content targeting my 🏳️🌈 and 🏳️⚧️ friends (among others).
But I still want to reach people here, so will be posting basic updates w/ links off-site for discussion.
hachyderm.io/@chandlerc
Thoughts on predictors.fail/ over where I regularly post:
hachyderm.io/@chandlerc/1139…
(Reminder, I'm not active here, find me on hachyderm or bsky)
Really excited about what the team has accomplished here! Also, the post shares some really fun details of hardened libc++, huge credit to the #Clang, #LLVM, and libc++ community!
Excited to share our latest post on memory safety! We're tackling spatial safety in our massive C++ codebase by hardening libc++ *by default*. It adds bounds checks to things like std::vector, preventing a fair bit of out-of-bounds vulnerabilities: security.googleblog.com/2024…
Basically.
There may be some differences, but id generally expect us to have a borrow checker or something equivalent.
If it works, much more comprehensive, integrated, and incremental interop and even automated migration where possible.
Carbon is still early stages, but we're aiming to have a similar level of safety to Rust or Swift long term.
Chandler Carruth retweeted
Excited to share Google's memory safety strategy! We're working to build safer software by migrating to memory-safe languages like Rust as well as hardening our existing C++: security.googleblog.com/2024….
We'll be sharing more details in upcoming posts.
Proud to start sharing Google's strategy for tackling our remaining memory safety challenges: security.googleblog.com/2024…
High level, but it outlines the long-term strategy. We'll be sharing more detailed posts in this series.
#CPlusPlus #RustLang #CarbonLang
Yes, ASan and other sanitizers will complain.
You could also get unlucky and have mapped memory end. For example, with a string view of an exact page-sized string, but where it was shrunk to zero length at the end, you could easily have the one byte be on an unmapped page.
Amazing update to one of my favorite stories about memory safety from Android folks: security.googleblog.com/2024…
Degree to which memory safe languages reduces this category of exploitation, and lower the aggregate exploit severity of a product is remarkable.
hachyderm.io/@chandlerc/1131…
And the fourth amazing edition of the Carbon Copy, your newsletter for #CarbonLang, is out! github.com/carbon-language/c…
Chandler Carruth retweeted
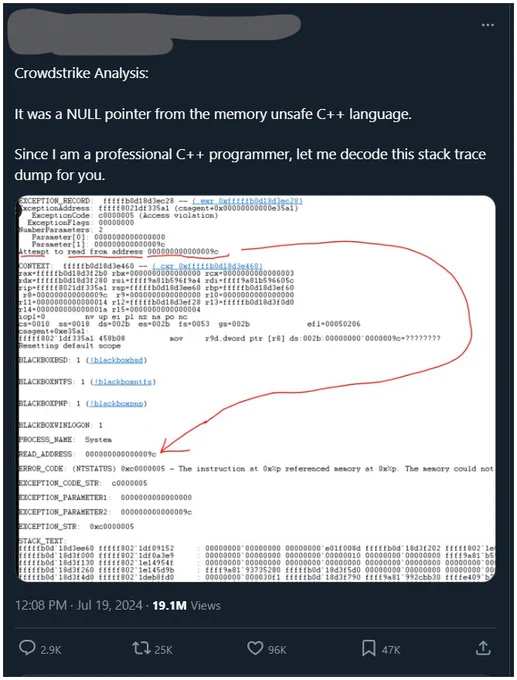
This strange tweet got >25k retweets. The author sounds confident, and he uses lots of hex and jargon. There are red flags though... like what's up with the DEI stuff, and who says "stack trace dump"? Let's take a closer look... 🧵1/n
Hot off the virtual presses is the 3rd edition of the Carbon Copy!! =D
I'm particularly excited about this one as it digs in a bit deeper into some meaty bits of the language design.
github.com/carbon-language/c…
#CarbonLang
Yeah, adding it afterward makes things harder, no doubt.
But we need to figure out how because we're starting with C++ which is already deeply unsafe, and interop is essential. So harder, but not avoidable IMO.
We have some good ideas tho, including making it a bit less painful
Carbon will definitely try to get to rigorous memory safety.
We're just starting with the C++ (thus unsafe) interoperable layer. We will then build up the safe end state and all the bridging needed to get there incrementally.
It's a sequencing thing, not lack of a goal.
We definition check variadics with symbolic arity. This also lets us definition check the variadic's arity being valid in all uses of the pack, etc.
The CppNow talk about this should be posted soon, and the proposal for it is under active work: github.com/carbon-language/c…
There are calling conventions that do callee-destruction of by-value parameters, which would make returning a reference to them dangle.
Chandler Carruth retweeted
New blog post: Notes from the Carbon panel session at EuroLLVM 2024. muxup.com/2024q2/notes-from-…