Suelo ignorar gente campeonamente.
Joined November 2010
- Tweets 7,984
- Following 847
- Followers 91
- Likes 31,011
I'm Castor Troy retweeted
Knowing how to write assembly is a skill you should learn, and these guys have a great resource for you!
I've debugged 10,000 lines of assembly for every line I've ever written... but writing assembly from scratch is a core computer science skill, I believe: even if you never use it.
Will you use it to write new code? Maybe not. But when you get dropped into a call stack without source code, at least you won't have to ask your Dad for help!
And the next thing you should do after learning to write ASM is to get a crisp understanding of what your C code actually compiles to. Like a switch() statement is often a jump table, but if you've never debugged one...
I'm Castor Troy retweeted
You explicitly state, right there, that the point of the disclosure is to put pressure on @FFmpeg, thanks for clarifying the purpose of the disclosure.
This is exactly the story I tell. You have the commons, managed by volunteers, and some guys come in and they say 'if you don't fix this barrier, I will report you to the city'.
You say that it is meant to balance interests. Whose interests? The @FFmpeg gang makes the software available with *no warrantee*, for free (no $$$).
You *do not get* to demand warrantees if you just grabbed the software off the Internet.
By doing so, you are throwing the system off balance. The security researchers get paid. The guys maintaining FFmpeg do not.
And as a response, the open-source developers are coming to the conclusion that security researchers are scum, that they are parasites. And that's precisely what too many security researchers are: they make a living off the free labor of open-source developers.
« The reason bugs are disclosed isn't to get credit. »
Of course it is. Let us not be naive. How could you get credit for a bug that is undisclosed ? How do you get on leaderboards if your bugs are undisclosed?
We understand how the security research world works: find impressive bugs, get famous. This requires that the bugs be disclosed.
There is no rational explanation for how the FFmpeg disclosure made anyone safer. The only purpose here is to gather fame.
Google went to the press and made a big fuss about these bugs just to balance competing interests? This had nothing to do with furthering the careers of these engineers?
If it was all about making us safer, that's what Google would have done, they would have patched the bugs, and then disclosed them, long after the patched version were available.
No. They went to the press and bragged about disclosing unpatched bugs.
It goes against the moral fiber of open-source software. That's not how it works.
I'm Castor Troy retweeted
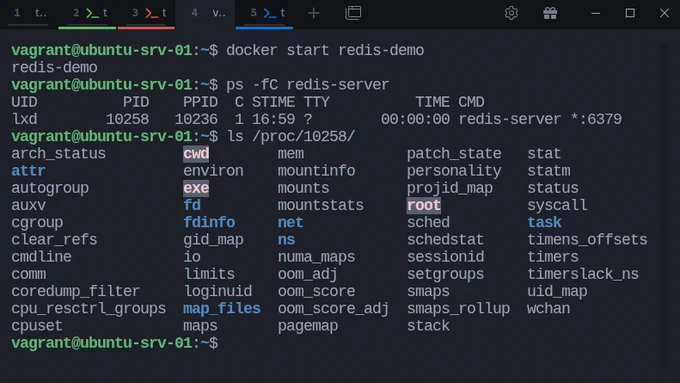
Part 3: Containers Are Just Linux Processes
In the previous part, we explored how PID namespaces isolate process trees, allowing each container to have its own “init” process and private view of running processes. Now that you understand how process isolation works at the kernel level, let’s zoom out for a moment.
Before moving on to network namespaces, it’s important to grasp a key concept: containers aren’t virtual machines or special kernel objects, they’re just ordinary Linux processes.
Tools like Docker, Podman, and containerd build on what the Linux kernel already provides. They bundle namespaces, cgroups, and a filesystem view into a single convenient abstraction and call that a container. But underneath, nothing extraordinary happens, the kernel is simply spawning and managing regular processes, just like it always has.
Learn in more in this guide:
blog.sysxplore.com/p/part-3-…
I'm Castor Troy retweeted
Want to understand B-trees better?
Try btree.app and bplustree.app.
These are standalone sandboxes of the visuals I built for my "B-trees and database indexes" article. Helpful for learning B-tree insertion, search, and node splits.
I'm Castor Troy retweeted
In case you haven't seen the article that goes with this: planetscale.com/blog/btrees-…
I'm Castor Troy retweeted
Learn Linux, networking, containers, and Kubernetes by solving hands-on problems 🛠️
A curated collection of over 100 carefully crafted challenges - with interactive checks, clear diagrams, and helpful theoretical references.
Like LeetCode but for DevOps labs.iximiuz.com/challenges
I'm Castor Troy retweeted
Funny how this Torvalds' quote fits perfectly with the @FFmpeg situation
I'm Castor Troy retweeted
Part 3: Containers Are Just Linux Processes
In the previous part, we explored how PID namespaces isolate process trees, allowing each container to have its own “init” process and private view of running processes. Now that you understand how process isolation works at the kernel level, let’s zoom out for a moment.
Before moving on to network namespaces, it’s important to grasp a key concept: containers aren’t virtual machines or special kernel objects, they’re just ordinary Linux processes.
Tools like Docker, Podman, and containerd build on what the Linux kernel already provides. They bundle namespaces, cgroups, and a filesystem view into a single convenient abstraction and call that a container. But underneath, nothing extraordinary happens, the kernel is simply spawning and managing regular processes, just like it always has.
Learn in more in this guide:
blog.sysxplore.com/p/part-3-…
The security guarantees of modern TEE offerings by Intel and AMD can be broken cheaply and easily, by building a memory interposition device that allows attackers to physically inspect all memory traffic inside a DDR5 server.
Source: tee.fail
I'm Castor Troy retweeted
"it's Python, you do anything and it allocates"
How true is this?
I modified CPython to print when it allocates an integer object
Then added numbers in a for-loop 100k times
My terminal got spammed with 101006 allocations
Why? Let's explore the internals of CPython:
I'm Castor Troy retweeted
Demostración de vulnerabilidad de cookies de sesión, donde un usuario normal puede modificar la petición HTTP y convertirse en un usuario con rol de administrador. #hackingetico #hackingweb #cookie #informatica